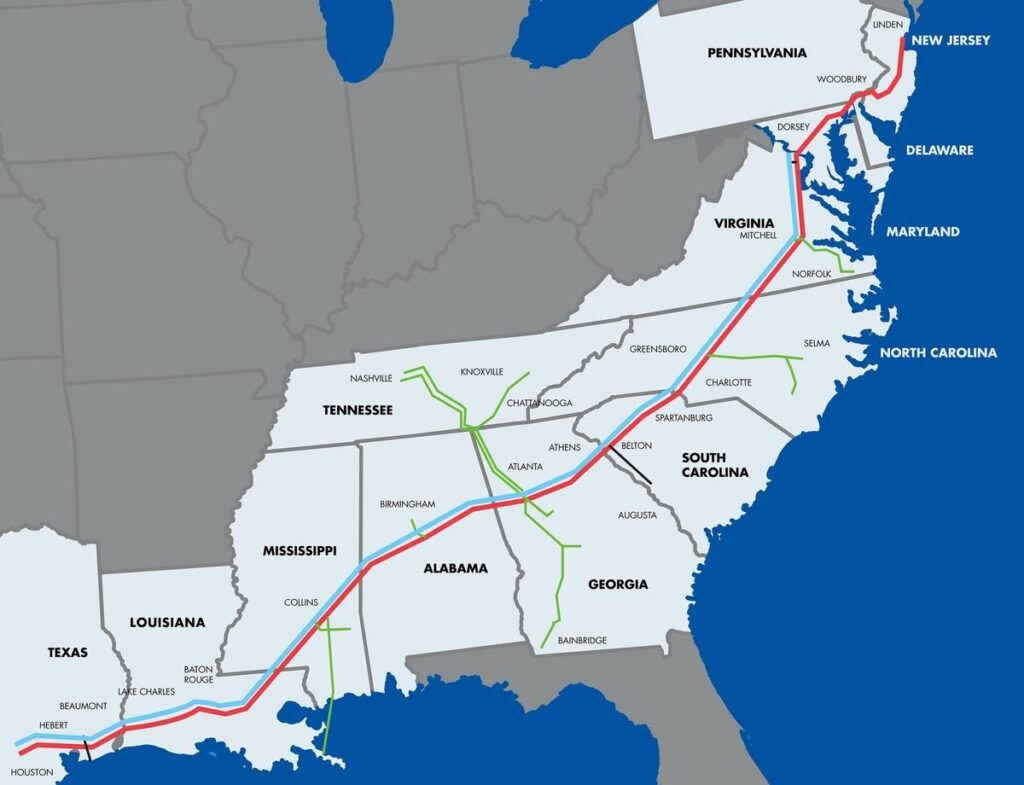
A major US fuel pipeline was forced to shut down after a suspected Chinese cyberattack on one of the largest pipelines in the United States, in what appeared to be a significant attempt to disrupt vulnerable energy infrastructure. The pipeline carries refined gasoline and jet fuel up the East Coast from Texas to New York.

The operator of the system, Colonial Pipeline, said in a statement late Friday 7-May, 2021 that it had shut down its 5,500 miles of pipeline, which it says carries 45 percent of the East Coast’s fuel supplies, in an effort to contain the breach on its computer networks. Earlier Friday, there were disruptions along the pipeline, but it was unclear whether that was a direct result of the attack, or the company’s moves to proactively halt it.

Colonial Pipeline indicated Saturday afternoon 8-May, 2021 that its systems were hit by ransomware, in which hackers hold a victim’s data hostage until it pays a ransom, or whether it was another form of cyberattack. The shutdown of such a vital pipeline, one that has been serving the East Coast since the early 1960s, highlights the huge vulnerability of aging infrastructure that has been connected, directly or indirectly, to the internet.

In coming weeks, the administration is expected to issue a broad-ranging executive order to bolster security of federal and private systems, after two major attacks from Russia and China in recent months caught American intelligence agencies and companies by surprise.
Colonial’s pipeline transports 2.5 million barrels each day, taking refined gasoline, diesel fuel and jet fuel from the Gulf Coast up to New York Harbor and New York’s major airports. Most of that goes into major storage tanks, and with energy use depressed by the coronavirus pandemic, the attack was unlikely to cause any immediate disruptions. It also serves some of the country’s largest airports, including Atlanta’s Hartsfield Jackson Airport, the world’s busiest by passenger traffic.
The incident is one of the most disruptive digital ransom operations ever reported and has drawn attention to how vulnerable U.S. energy infrastructure is to hackers. A prolonged shutdown of the line would cause prices to spike at gasoline pumps ahead of peak summer driving season, a potential blow to U.S. consumers and the economy.
In the statement, the company said that it learned on Friday that it “was the victim of a cybersecurity attack,” but it provided no details. Such an attack could involve malware that shut down its operations or ransomware demanding payment to unlock computer files or systems.

“In response, we proactively took certain systems offline to contain the threat, which has temporarily halted all pipeline operations, and affected some of our I.T. operations,” the company said, referring to information technology systems.
It said it had contacted law enforcement and other federal agencies. The F.B.I. leads such investigations, but critical infrastructure is the responsibility of the Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency. An administration official said that an investigation into the episode was in the very early stages, and that it was unclear whether the attacker was a nation or a criminal group. At times, they work in concert.

Attacks on critical infrastructure have been a major concern for a decade, but they have accelerated in recent months after two breaches — the SolarWinds intrusion by Russia’s main intelligence service, and another against some types of Microsoft-designed systems that has been attributed to Chinese hackers — underscored the vulnerability of the networks on which the government and corporations rely.
The pipeline attack could be a litmus for the Biden administration’s overall cyber strategy, which has been slowly taking shape – and, at least in public, has largely focused on responding to Russian and Chinese cyber-espionage campaigns that were wide-ranging but fell short of physical sabotage. So far, the administration‘s major tools have been sanctions and indictments, as seen in an executive order that Biden issued last month in response to Russia’s SolarWinds cyber campaign. However no such sanctions were announced against China for cyber attack against some types of Microsoft-designed systems that has been attributed to Chinese hackers.
Related Article Chinese Hackers Hack into Pfizer-BioNTech Vaccine Data In Europe
For that reason, understanding how the pipeline attack unfolded — and the motivations of those behind it — will become the focus of federal investigators and the White House, which has elevated cybervulnerabilities to the top of its national security agenda.
As a privately held company, Colonial is under less pressure than a public company might be to reveal details. But its statement left unclear whether the initial attack was directed at the industrial controls that are used to manage the pipeline — which most large utility operators keep insulated from the internet to reduce their vulnerability — or whether it was a ransomware attack that stole or froze data on Colonial’s computer systems.
People familiar with the investigation said the early indications were that it was a ransomware attack, and that the events had been unfolding for several days. The company has hired the private cybersecurity firm FireEye, which responded to the hacking of Sony Pictures Entertainment, energy facility breaches in the Middle East and many federal government incidents.
The company appears to have brought down activity on the pipeline on Friday to prevent the hackers from inflicting more damage. But that left open the question of whether the attackers themselves now have the ability to directly turn the pipelines on or off, or trigger operations that could cause an accident.
If it was a ransomware attack, it would be the second known such incident aimed at a pipeline operator. Last year, the Cybersecurity and Infrastructure Security Agency reported a ransomware attack on a natural gas compression facility belonging to a pipeline operator. That forced a shutdown of the facility for two days, though the agency never revealed the company’s name.
Cybersecurity experts say the rise of automated attack tools and cryptocurrencies, which make it harder to trace perpetrators, has exacerbated ransomware attacks.
“We’ve seen ransomware start hitting soft targets like hospitals and municipalities, where losing access has real-world consequences and makes victims more likely to pay,” said Ulf Lindqvist, a director at SRI International, who specializes in threats to industrial systems. “We are talking about the risk of injury or death, not just losing your email.”
It is unclear how long the pipeline will be shut down, and so far the effect on fuel prices has been small, with gasoline and diesel futures rising about 1 percent on the New York Mercantile Exchange on Friday. Prices for regular gasoline at the pump in New York State rose on Saturday by a penny, to $3 from $2.99. Over the past week, gasoline prices have risen nationwide by 6 cents, as global oil prices have risen rapidly.
“It’s a serious issue,” said Tom Kloza, the global head of energy analysis at Oil Price Information Service. “It could snarl things up because it is the country’s jugular aorta for moving fuel from the Gulf Coast up to New York.”
“This is as close as you can get to the jugular of infrastructure in the United States,” said Amy Myers Jaffe, research professor and managing director of the Climate Policy Lab. “It’s not a major pipeline. It’s the pipeline.”
The Oil Price Information Service reports that American gasoline inventories are at the “comfortable” levels of 235.8 million barrels, nearly 10 million barrels above levels in 2019, before the pandemic reduced demand for fuel. Middle Atlantic and New England states have substantial supplies, the analysis service reported.
Prices at the pump could be affected in different ways depending on the region. If there is a prolonged shutdown, Alabama north through Baltimore will potentially see shortages. However, Midwestern and Ohio Valley states could actually benefit from cheaper shipments from the gulf refineries as the plants divert stranded supplies.
Colonial Pipeline, based in Alpharetta, Ga., is owned by several American and foreign companies and investment firms, including Koch Industries and Royal Dutch Shell. The pipeline connects Houston and the Port of New York and New Jersey and also provides jet fuel to most of the major airports, including in Atlanta and Washington, D.C.
Though both the SolarWinds and the Microsoft attacks appeared aimed, at least initially, at the theft of emails and other data, the nature of the intrusions created “back doors” that experts say could ultimately enable attacks on physical infrastructure. So far, neither effort is thought to have led to anything other than data theft, though there have been quiet concerns in the federal government that the vulnerabilities could be used for infrastructure attacks in the future.
The Biden administration announced sanctions against Russia last month for SolarWinds, and the executive order it is expected to issue would take steps to secure critical infrastructure, including requiring enhanced security for vendors providing services to the federal government.
The United States has long warned that Russia has implanted malicious code in the electric utility networks, and the United States responded several years ago by putting similar code into the Russian grid.
But actual attacks on energy systems are rare. About a decade ago, Iran was blamed for an attack on the computer systems of Saudi Aramco, one of the world’s largest oil producers, which destroyed 30,000 computers. That attack, which appeared to be in response to the American-Israeli attack on Iran’s nuclear centrifuges, did not affect operations.
Another attack on a Saudi petrochemical plant in 2017 nearly set off a major industrial disaster. But it was shut down quickly, and investigators later attributed it to Russian hackers. This year, someone briefly took control of a water treatment plant in a small Florida city, in what appeared to be an effort to poison the supply, but the attempt was quickly halted.
Social Media has blamed China for the Cyber Attacks on the pipeline because only China has the motives to create disruptions in United States because China perceives US as a threat in case China invades Taiwan.
Chinese hackers have a long history of doing it in the past
Over the past two decades, the People’s Republic of China (PRC) has capitalized on the global connectivity of the internet age in ways no other nation has. Once regarded as a “second-tier” cyber power, China has aggressively and consistently built its national cyber program to the point where it is now considered one of the world’s preeminent cyber players.
As the Chinese military and intelligence apparatus became more cyber-capable, units within the People’s Liberation Army and contractors operating on behalf of the Ministry of State Security embarked on a systematic cyber espionage campaign. China obtained sensitive information held by foreign governments and stole intellectual property for cutting-edge technologies across numerous sectors by leveraging cyber alongside traditional intelligence collection methods and various forms of economic espionage. The campaign has, by any measure, been immensely successful.
China has directly utilized the information it has obtained via cyber espionage to improve its military capabilities.
Reuters has previously reported on allegations that hackers linked to North Korea, South Korea, Iran, Vietnam, China and Russia have on separate occasions tried to steal information about the virus and potential treatments.
In September 2020, Federal prosecutors indicted two Chinese nationals on hacking charges and said the men had been trying to break into networks at a Maryland biotech firm and a Massachusetts biotech firm. Both firms were publicly known at the time of the hack to be working on COVID-19 vaccines.
In July 2020, two state-sponsored hackers in China targeted US businesses in a “sophisticated and prolific threat” for more than 10 years, both for financial gain and to steal trade secrets, the Department of Justice said.
The 11-count indictment, which was made public, alleges Li Xiaoyu and Dong Jiazhi worked with China’s Ministry of State Security (MSS) and other agencies to hack into “hundreds of victim companies, governments, non-governmental organizations, and individual dissidents, clergy, and democratic and human rights activists in the United States and abroad.” The 11-count indictment in PDF format can be downloaded here:-
gov.uscourts.waed_.91446.15.0Li and Dong were allegedly infiltrating networks of businesses in a wide array of sectors, including “high tech manufacturing; civil, industrial, and medical device engineering; business, educational, and gaming software development; solar energy; and pharmaceuticals,” as well as defense contractors, since at least September 2009. In recent months, prosecutors allege, the two were seeking ways in to “the networks of biotech and other firms publicly known for work on COVID-19 vaccines, treatments, and testing technology” in at least 11 countries, including the US.
APT 41 and BARIUM Chinese Hackers Groups
In September 2020 itself, A US Federal Court indicted 5 Chinese Hackers of APT 41 and BARIUM Group Working for Chinese Ministry of State Security for the theft of source code, software code signing certificates, customer account data, and valuable business information. We covered it in details in our previous article US Federal Court Indicted 5 Chinese Hackers of APT 41 and BARIUM Group Working for Chinese Ministry of State Security
TA410 Chinese Hackers Group
In July 2019, several U.S. utility companies were targeted with a well-designed spearphishing campaign that impersonated a legitimate engineering licensing board to deliver the LookBack malware. This campaign was attributed to a group tracked as TA410, who proceeded to conduct a follow-on campaign once again targeting U.S. electric utilities in August of that year. Later media reports indicated that several smaller, regional public power utilities were among those targeted and that some were apparently unaware they had been targeted at all until they were informed by the FBI.
Additional analysis later linked the LookBack phishing campaigns to another malware family dubbed FlowCloud. These two campaigns share a number of tactics, including the timeframes they were active, the use of malicious attachments contained in phishing emails, the installation techniques used, and overlapping infrastructure. Like LookBack, the FlowCloud campaign appears to have targeted victims in the utilities sector using well-crafted phishing emails impersonating professional organizations within the industry such as the American Society of Civil Engineers.
Notably, the researchers investigating TA410 identified similarities to the tactics used by TA429 (also known as APT10). However, it is not fully clear whether the two groups’ activity is truly related or whether this may have been a deliberate attempt by those responsible to plant “false flags” to help hide those behind the campaigns. The attempt to hide the campaign actors makes sense especially given the widespread media attention focused on APT10 due to the publication of multiple reports on the group and a related U.S. indictment of Chinese actors.
Chinese Thousand Talents Program
Not only hacking, Chinese CCP has stolen the research of other countries on cure for Chinese Corona Virus and jeopardized their efforts to develop a vaccine for cure of Chinese Corona Virus COVID-19. We covered it in details in our previous article Justin Trudeau’s Love For China Puts Canadians at Risk : Chinese “Thousand Talents” Program Robs Canada of the Research Canada had Invested In
Reuters has documented that espionage campaigns targeted a slew of pharmaceutical and vaccine development companies including Gilead, Johnson & Johnson, Novavax, and Moderna. Regulators and international organizations such as the World Health Organization have also come under repeated attack.
“Vaccine candidates represent liquid gold to many parties, both in terms of the opportunity and the pure market value,” said Rogers, who is also vice president at security company Okta Inc. “Information on the vaccine and access to any link in the distribution chain has significantly increased value.”
The respiratory virus, which emerged in China in late 2019, has infected more than 68 million people worldwide, according to a Reuters tally. More than 1.5 million people have died.
Related Article Countering the Chinese Communist Party’s Covert, Coercive, Corrupting and Malign Influence in Free Societies : US State Department
Points to Ponder
After the Bio-Warfare attack on the whole world that killed over 3.28 million people worldwide and brought the world economy to a stand still, China still continues to disrupt economic activity in other countries in order to destroy any possible adversaries. Shouldn’t China be boycotted by all the countries?
Were the policies of President Trump to corner China and impose sanctions not better than the present Biden Administration which has not imposed any sanctions against China?
Follow us at:-
Twitter Handle: @newscomworld
Twitter Handle for Hindi : @NewsWorldHindi
Telegram Handle : @NewsComWorldCom
Koo Handle : @NewsComWorld
Parler Handle: @NewsComWorld
Tooter Handle: @NewsComWorld
YouTube Channel https://www.youtube.com/channel/UCnKJQ3gFsRVWpvdjnntQoAA
Facebook Page https://www.facebook.com/NewsComWorld
1,744 total views








